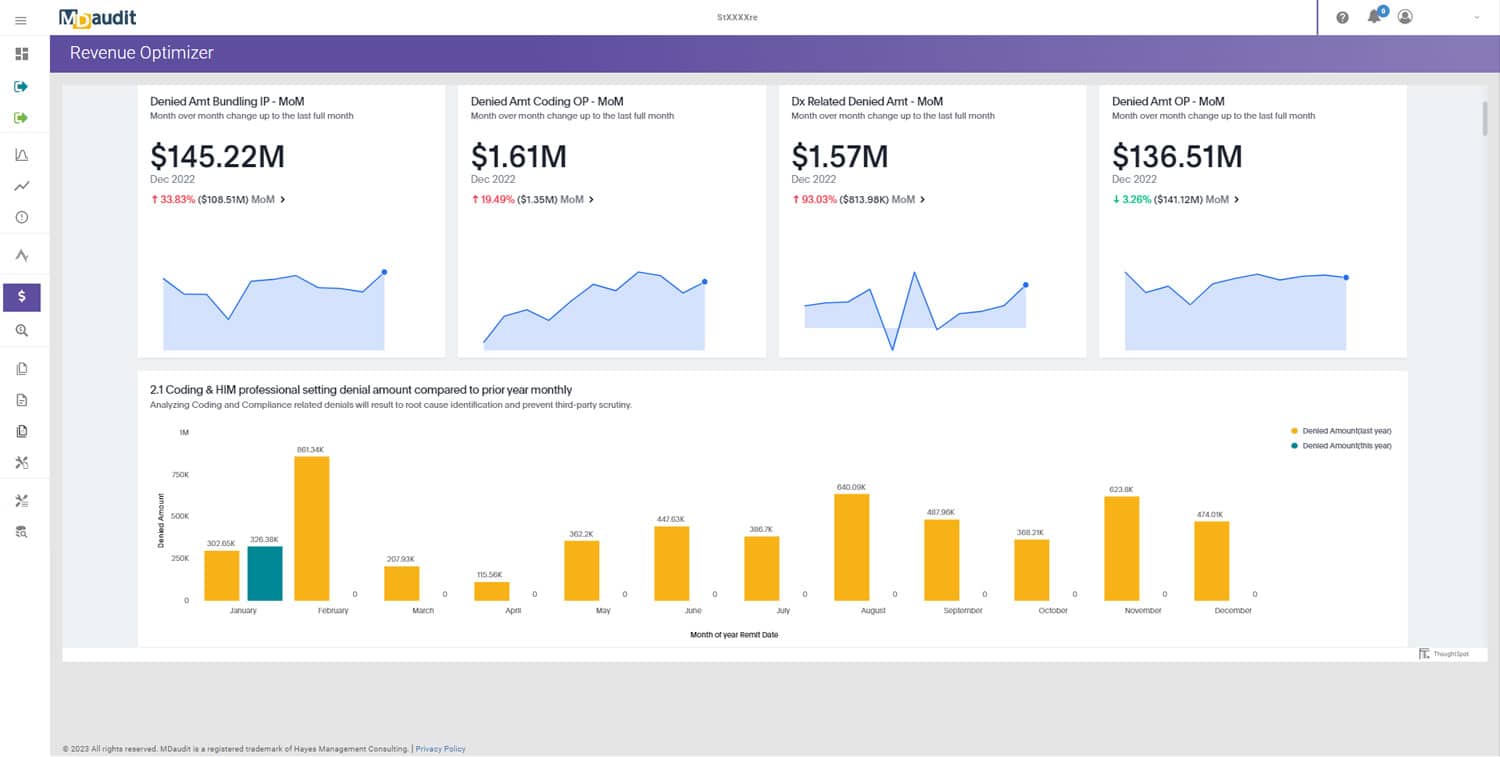
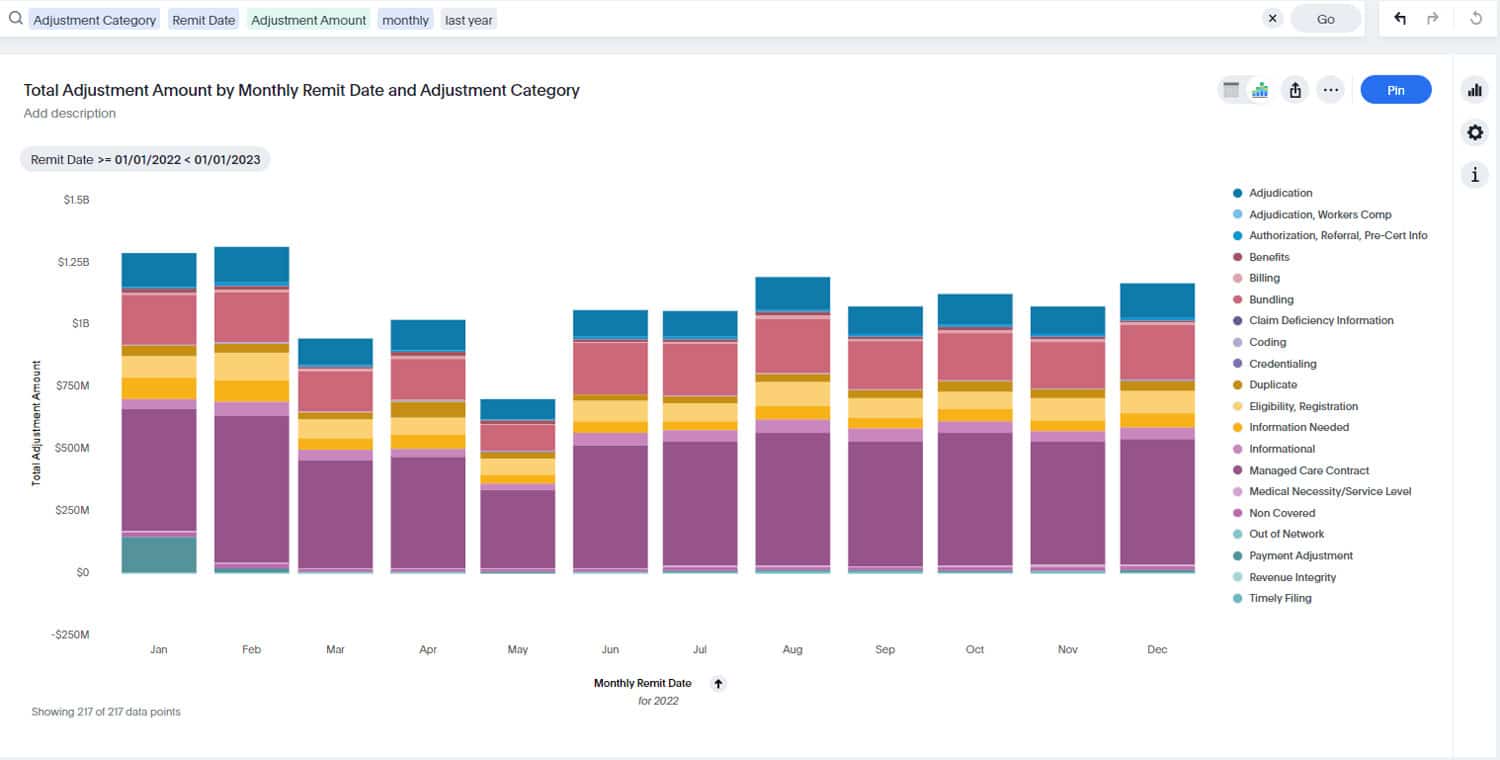
With tens of millions of patient records being breached each year – and hacking responsible for more than three-quarters of those incidents – healthcare organizations must pay particular attention to the security of their technology systems, including billing compliance software.
Last year, just under 700 breaches affected 51.4 million records — the highest total outside the anomalous 2015, when just two breaches hit nearly 90 million records. In February 2023 alone, nearly 5.5 million records were breached in 33 incidents, including 17 breaches of more than 10,000 records. Hacking accounted for 77% of all breaches and more than 99% of all breached records.
“Hackers can exploit nearly any security vulnerability, so it’s critical that hospitals and health systems thoroughly assess each technology vendor in their portfolio,” says Raj Joshi, Chief Information and Security Officer at MDaudit. “Look for companies that take security seriously, hold national technology certifications, and readily share their security protocols.”
When evaluating billing compliance software or other technology, look for the following security features.
1. HIPAA compliance.
Admittedly, this is a low bar to clear. Any software that stores, transmits or accesses patient data must adhere to the HIPAA Privacy Rule regarding protected health information (PHI). Examine the security protocols of any vendor closely to ensure compliance.
2. Secure cloud storage.
Many software systems are Software-as-a-Service (SaaS), relying on cloud-based data centers to process, store, and transmit PHI. As part of your due diligence, discover what data centers a vendor uses, and ask questions about their security protocols. Insist on such factors as:
- Leveraging encryption to manage all confidential information
- Data should be encrypted at rest (AES-256) and in transit (TLS 1.2)
- Robust monitoring, storage, and access to log files
- Ensuring access to infrastructure based on roles and responsibilities only
- Practicing the principle of least privilege access
As well as an audit trail to enable governance, compliance, operational auditing, and risk auditing.
3. Multifactor authentication (MFA).
MFA has become the gold standard for login protocols, requiring two or more identity factors uniquely accessible by each user. Credentials are based on three categories: something users know (e.g., password or PIN), something users possess (e.g., physical security key or smart card), or something users embody (e.g., fingerprint). Certification bodies and cyber insurance companies are increasingly requiring MFA.
4. Single sign-on (SSO) authentication.
SSO enhances user access controls and simplifies configuration and maintenance for customers by combining several application login screens into one — a particular advantage in a busy hospital environment. SSO also allows IT staff to:
- Enforce stronger passwords leveraging stringent protocols
- Enable multifactor authentication
- Impose session expiration duration
With SSO, users and IT administrators spend less time entering, reentering, recovering, and resetting passwords, eliminating frustration, and increasing productivity.
5. Industry certification.
Vendors are in the business of selling software, which leads some to downplay potential vulnerabilities in their systems. Look for third-party certifications from organizations such as HITRUST CSF, which leverages nationally and internationally accepted security and privacy-related regulations, standards, and frameworks into a consistent framework. The standard uses ISO, NIST, PCI, HIPAA, and GDPR to ensure security and privacy controls, dynamically incorporating other sources.
6. Infrastructure security measures.
Always scrutinize the types of infrastructure security measures that are in place by asking such key questions as:
- Is penetration testing performed on the network to uncover potential vulnerabilities, and, if so, how often?
- Is the test performed internally or by an independent party?
Other infrastructure security measures to check for include geo-filters to reduce global cyber-attacks and application-level audit trails that log access related to PHI.
7. Data standards.
Make sure your vendor uses widely accepted electronic data interchange (EDI) standards such as ANSI ASC X12, developed by the Accredited Standards Committee, supporting a variety of X12 transactions such as institutional, professional, remittance, and claim files (837/I/P/D and 835s).
8. Disaster recovery and business continuity.
Any downtime can have dramatic consequences for hospitals and health systems — even in the billing department. Thoroughly investigate a vendor’s disaster recovery and business continuity postures. How often do backups occur, and where are they stored? What happens if a data center goes offline? Insist on daily backups of all storage volumes and daily backups of the entire server and keep a copy of the backups at separate cloud zone. Test out BCP and DR plans annually to ensure the procedures and scripts are functional and working as designed.
Demand the highest security for your billing compliance software
Every technology component in a hospital or other healthcare organization is critically important, including billing compliance software. The weakest link in the technology chain can be the entry point for hackers to seize control of data, crippling operations and disrupting patient care. Proper due diligence that includes checking adherence to the highest standards of data security outlined in these eight tips goes a long way to helping hospitals make good technology decisions.
Although security is likely the most important aspect of selecting a solid vendor, there are many other things to consider. Check out these 6 Pitfalls You Need to be Aware of When Selecting Billing Compliance and Audit Software.